Eight years of Sender Policy Framework (SPF)

Sender Policy Framework (SPF) is used to authenticate senders of email. Receiving servers use SPF to verify if the message source IP is authorized to send on behalf of the HELO or MAIL FROM domain.
History
The first draft of the Sender Policy Framework was written in December 2004 and became RFC4408 precisely 16 years ago in April 2006. In 2011 a new draft was created that became the RFC7208 in April 2014 that we use today. To celebrate its 8th anniversary, we've taken a look at the SPF implementation amongst the top 600.000 domains.
Scanning
We've written an extensive script that detects the presence of an SPF policy and checks for syntax and configuration errors. If you want to test and validate your domain's SPF policy, you can use our free SPF validation tool.
Results
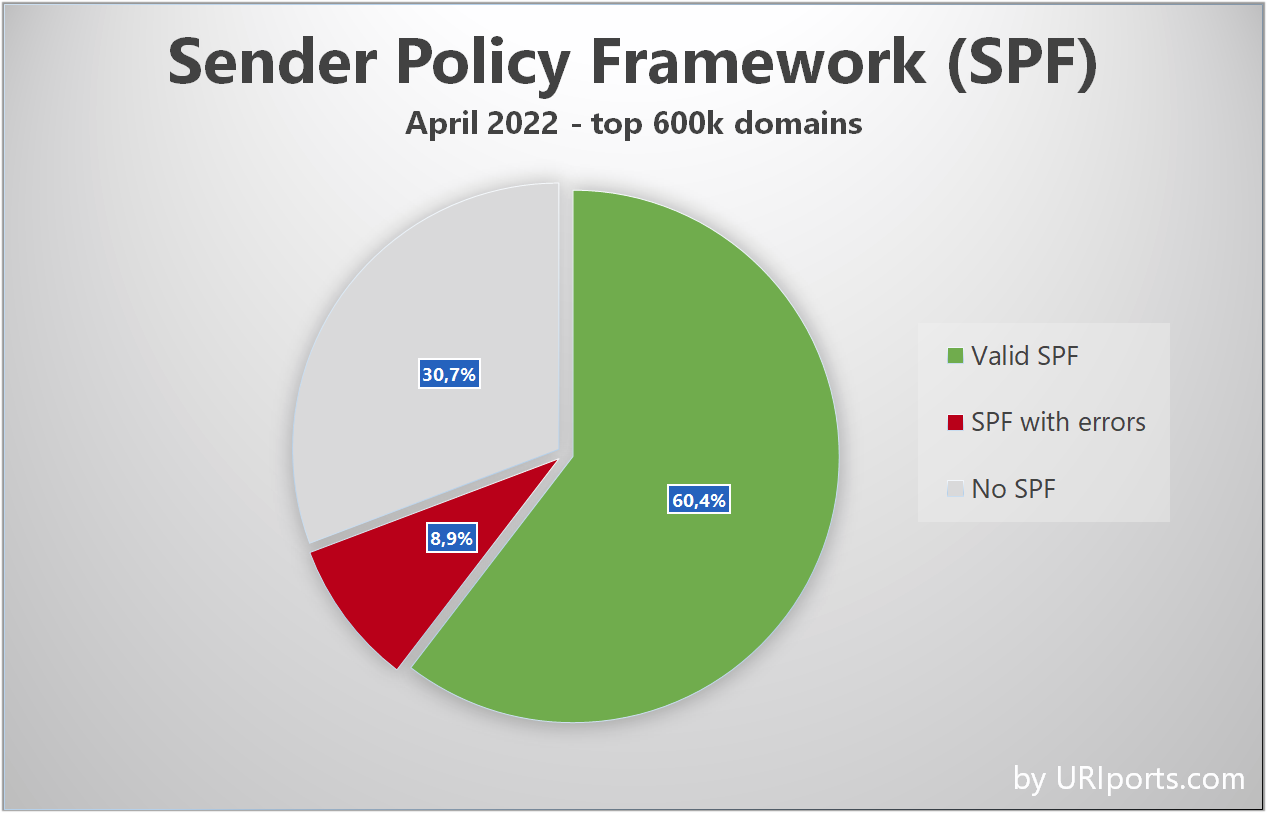
It turns out that 60,4% of the tested domains have a valid SPF policy, while 30,7% do not have an SPF policy (yet). Unfortunately, that leaves 8.9% of SPF policies with configuration errors.
Common Issues
A complete list of all the issues we've encountered is specified below. I will also explain what causes them and offer a solution where possible.
Maximum DNS-interactive terms limit exceeded (58.2%)
The SPF standard specifies a maximum of 10 DNS lookups to be used to resolve a policy to prevent abuse and attacks. Domains can implement SPF macros or use subdomains for third-party email services allowing a separate SPF policy to avoid hitting the DNS lookup limit.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-4.6.4
Example (twitch.tv): https://www.uriports.com/tools?method=spf&domain=twitch.tv
Redundant sender policies (25.9%)
When a hostname publishes multiple TXT records that start with the v=spf1 element, none of the policies are processed, causing SPF to fail.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-3.2
Example (huffingtonpost.com): https://www.uriports.com/tools?method=spf&domain=huffingtonpost.com
Junk encountered (5.2%)
If an SPF policy syntax is incorrect, the policy is not processed, and a permerror is returned. The most common cause for this error is the absence of whitespace (ip4:x.x.x.xinclude:_spf.example.com instead of ip4:x.x.x.x include:_spf.example.com).
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-4.6.1
Example (zdnet.com): https://www.uriports.com/tools?method=spf&domain=zdnet.com
Unknown mechanism type (3.7%)
An SPF policy will fail whenever an unknown mechanism is found. This is usually caused by excessive whitespace (ip4: x.x.x.x instead of ip4:x.x.x.x) or typos in the mechanism (ipv4 / ipv6 instead of ip4 / ip6).
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-5
Example (greasyfork.org): https://www.uriports.com/tools?method=spf&domain=greasyfork.org
Maximum void DNS lookups limit exceeded (2.8%)
The SPF standard specifies a maximum of 2 void lookups. Therefore, SPF will fail when it triggers two or more DNS lookups that do not return any results.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-4.6.4
Example (barnesandnoble.com): https://www.uriports.com/tools?method=spf&domain=barnesandnoble.com
SERVFAIL error on DNS MX / A / TXT lookup (2.1%)
Whenever an SPF refers to a record that does not exist (anymore), a SERVFAIL error is triggered, causing an SPF temperror. This is caused mainly by obsolete entries in the SPF but could also be caused by temporary connectivity issues.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-8.6
Example (dollarshaveclub.com): https://www.uriports.com/tools?method=spf&domain=dollarshaveclub.com
Missing required domain-spec (2%)
The include mechanism requires a hostname value that publishes an SPF record. Errors occur when this value is missing or contains an invalid value like an IP address.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-5.2
Example (visitsealife.com): https://www.uriports.com/tools?method=spf&domain=visitsealife.com
Invalid IPv4 / IPv6 prefix length encountered (< 0.1%)
Mechanisms ip4 and ip6 can specify a CIDR length. The maximum IPv4 CIDR value is 32 and 128 for IPv6. An SPF permerror is returned when this value is exceeded. The most common mistake is when people use the / symbol to define a range (ip4:218.4.237.183/184).
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-5.6
Example (greatergood.org): https://www.uriports.com/tools?method=spf&domain=greatergood.org
Duplicate global modifier 'redirect' encountered (< 0.1%)
The redirect modifier can only be specified once in an SPF policy. A permerror is returned when multiple redirects are specified.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-6.1
Example (jowi.club): https://www.uriports.com/tools?method=spf&domain=jowi.club
+all (0.6%)
Although technically correct, having an SPF policy that contains +all will allow anyone to send emails on behalf of the domain. 330 domains publish or include an SPF policy with either all or +all.
Details: https://datatracker.ietf.org/doc/html/rfc7208#section-5.1
Example (ubuntu.com): https://www.uriports.com/tools?method=spf&domain=ubuntu.com
Settings up an SPF policy is not a set-and-forget task. Keeping your SPF working requires regular updates and maintenance. URIports offers excellent tools that validate and verify your SPF policy regularly and automatically. You will also receive push notifications whenever issues are detected. Start your free 30-day trial now!

